I tried generating new keys, using existing keys, copying exactly the same /.ssh directory used by git on my Windows machine, and nothing made any difference on the Mac. I've had an ssh key I've used for some time to access my server from the Mac, which I thought was the idrsa/idrsa.pub pair in /,ssh.
I understand that since Mac OS X Leopard the Keychain has supported storing SSH keys. Could someone please explain how this feature is supposed to work.
I have some RSA keys that I've generated stored in my ~/.ssh directory for accessing various servers. I don't have passphrases set on those keys. Currently in order to log in to those servers I use the following commands in the Terminal:
(I've written some Bash functions to make this easier.)
Is there a better way to do this using the Keychain?
 John TopleyJohn Topley
John TopleyJohn Topley9 Answers
For it to work, the $SSH_AUTH_SOCK environment variable should be pointed to /tmp/launch-xxxxxx/Listeners. This is supposed to be done automatically when you log in. The listener on that socket speaks the ssh-agent protocol.
Your bash scripts are starting your own ssh agent (spelled ssh-agent, not ssh_agent) and overriding the existing ssh-agent that is set up for you at login.
Also, the whole point of the keychain is to store the passwords to your ssh keys, but you say that you don't have passphrases set on those keys, so I'm not sure what you are expecting out of the keychain integration.
Finally, when you first log in, you probably won't see a ssh-agent process. That process will be started automatically by launch services the first time something tries to read that socket in /tmp.
As of the Leopard release of OS X, ssh-agent is more tightly integrated with Keychain. It is possible to store the passphrases of all of your SSH keys securely in Keychain, from which ssh-agent will read them on startup. The bottom line is that it is simple to secure your keys with passphrases, but never have to type the passphrase to use them! Here is how:
Add the pass phrase to each ssh key to keychain: (option -k loads plain private keys only, skips certificates)
(note that's a capital K)
Whenever you reboot your Mac, all the SSH keys in your keychain will be automatically loaded. You should be able to see the keys in the Keychain Access app, as well as from the command line via:
jeffmccjeffmcc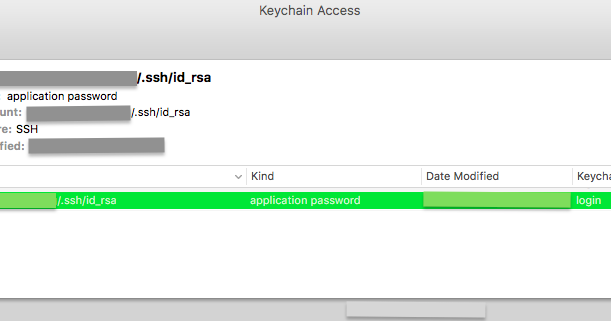
As of macOS Sierra, ssh-agent no longer auto-loads previously loaded ssh keys when you log in to your account. This is intentional on Apple part, they wanted to re-align with the mainstream OpenSSH implementation. [1]
As explained here, this is the recommended method since macOS 10.12.2:
Add the following lines to your
~/.ssh/configfile:Any key you add to the ssh-agent using the
ssh-add /path/to/your/private/key/id_rsacommand will be automatically added to the keychain, and should be autoloaded upon reboot.
The following is deprecated (kept for reference).
To go back to the previous behavior, you'd want to run the ssh-add -A command (which auto-loads all the ssh keys that have pass-phrases on your keychain) when you log in. To do that, follow these steps:
First, add all the keys you want to auto-load to the ssh-agent using the
ssh-add -K /absolute/path/to/your/private/key/id_rsacommand. The-Kargument ensures that the key pass-phrase is added to macOS's keychain. Make sure you use the absolute path to the key. Using a relative path will make the auto-launched script not to find your key.Make sure all of your keys are shown as added when you type
ssh-add -A.Create a file called
com.yourusername.ssh-add.plistin~/Library/LaunchAgents/with the contents below. Plist files such as this one are used bylaunchdto run scripts when you log in. [2][3]Tell
launchdto load the plist file you just created by executing:launchctl load ~/Library/LaunchAgents/com.yourusername.ssh-add.plist.
And you should be all set.
There is a simpler way than Ricardo's answer to persist your password between sessions/restarts of your Mac running 10.12 Sierra.
ssh-add -K ~/.ssh/id_rsa
Note: change the path to where your id_rsa key is located.ssh-add -ACreate (or edit if it exists) the following
~/.ssh/configfile:Now the password is remembered between restarts!
Apple purposely changed the behaviour for ssh-agent in macOS 10.12 Sierra to no longer automatically load the previous SSH keys, as noted in this OpenRadar, Twitter discussion, and Technical Note from Apple. The solution above will mimic the old behaviour of El Capitan and remember your password.
Note: for macOS Sierra, please refer to the more recent answer by ChrisJF.
The [answer by Jeff McCarrell][2] is correct, except that the command to add the pass phrase contains an en dash instead of a hyphen, i.e. –K instead of -K, causing a message to the effect of –K: No such file or directory.It should read:
I suspect you aren't using the default ssh command. Do you have ssh installed via ports? Try which ssh to see which ssh command you are using.
Usually it should display a dialog box asking for you password, if it isn't already stored in you keychain.
OllyOllyI had a similar problem while trying to login using a client ssh cert. In this specific case it was for accessing a git repository. This was the situation:
Mac Ssh Key
- Key was saved in
~/.ssh/ - The private key has a passphrase.
- The passphrase is stored in the OS X login keychain.
~/Library/Keychains/login.keychain - The connection was as follows: my mac
->remote mac->git/ssh server - Mac OS X 10.8.5
When I connected to remote mac using remote desktop, I didn't have a problem. However when connecting with SSH to the remote mac, I was asked for the ssh passphrase every time. The following steps solved it for me.
security unlock-keychainThe passphrase is stored in the login keychain. This unlocks it and enables ssh-agent to access it.eval `ssh-agent -s`Starts ssh-agent for shell use. It will get the passphrase from the keychain and use it to unlock the private ssh key.- Establish the ssh/git connection and do my work.
eval `ssh-agent -k`Kill the running ssh-agent.security lock-keychainLock the keychain again.
See also:
... adding this note as more detail was requested: the 'security' command is capable of importing keys (and other things) directly into Keychains. The nice thing is that unlike ssh-add, you are able to specify the keychain. This makes it possible to import directly into the system Keychain ('man security' to learn how)
The best and Apple intended solution (since macOS 10.12.2) is described here
Find Ssh Key In Mac Manual 2017

So just do the following:
echo 'UseKeychain yes' >> ~/.ssh/config